Fuzzing, at its core, involves feeding unexpected or random inputs into a system to uncover potential security flaws. The Flipper Zero, a portable, multi-tool device, is designed to interact with a wide range of digital interfaces, making it particularly adept at fuzzing tasks. Its user-friendly interface and powerful features enable users to experiment with different fuzzing techniques, providing insights into the robustness of their systems. This ability to simulate various attack vectors makes the Flipper Zero a key player in the field of fuzzing. The importance of fuzzing cannot be overstated, as it helps to identify weaknesses before they can be exploited by malicious actors. By leveraging the capabilities of the Flipper Zero, users can gain a deeper understanding of their system's vulnerabilities, allowing them to implement necessary safeguards. This article delves into the intricacies of flipper zero fuzzing, providing a detailed exploration of its methods, benefits, and applications in cybersecurity. Whether you're a seasoned professional or a curious beginner, this guide will equip you with the knowledge needed to harness the full potential of the Flipper Zero for fuzzing endeavors.
Table of Contents
- What is Fuzzing?
- The Flipper Zero: An Overview
- How Does Flipper Zero Fuzzing Work?
- Why Use Flipper Zero for Fuzzing?
- Key Features of Flipper Zero
- Preparing for Fuzzing with Flipper Zero
- Step-by-Step Guide to Flipper Zero Fuzzing
- Common Fuzzing Techniques
- Flipper Zero Fuzzing in Cybersecurity
- Challenges and Limitations of Flipper Zero Fuzzing
- Real-world Applications of Flipper Zero Fuzzing
- The Future of Flipper Zero Fuzzing
- Best Practices for Effective Fuzzing
- FAQs about Flipper Zero Fuzzing
- Conclusion
What is Fuzzing?
Fuzzing, a cornerstone of cybersecurity, is a testing technique used to identify vulnerabilities in software and hardware systems. By introducing unexpected or random inputs to a system, fuzzing aims to uncover security flaws that might otherwise remain undetected. This proactive approach is essential in mitigating risks, as it helps developers and security professionals address potential issues before they can be exploited by malicious actors.
The process of fuzzing involves generating inputs that range from slightly incorrect to completely random, observing how the system responds to these anomalies. The primary goal is to trigger unintended behavior or crashes, which may indicate vulnerabilities. Fuzzing is widely used in software development and cybersecurity due to its effectiveness in identifying bugs and vulnerabilities that traditional testing methods might miss.
Read also:Why Does Cancer Itch Unraveling The Mysteries Behind This Symptom
One of the key advantages of fuzzing is its ability to automate the testing process, allowing for the efficient examination of large codebases or complex systems. By continuously generating and testing inputs, fuzzing can provide comprehensive coverage, ensuring that even obscure vulnerabilities are identified and addressed. This makes it an invaluable tool in the ongoing effort to secure digital systems against potential threats.
The Flipper Zero: An Overview
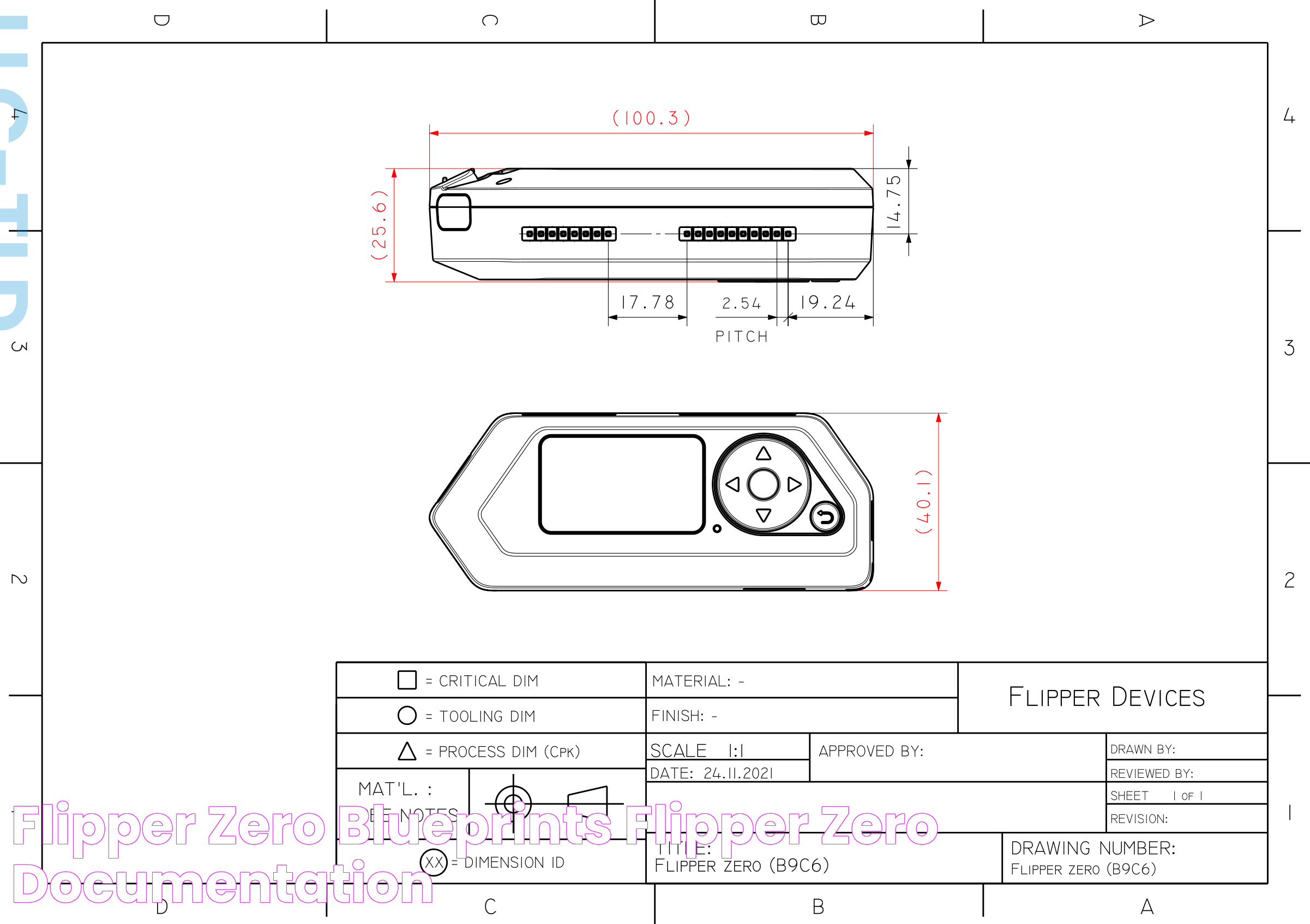
The Flipper Zero is a versatile, handheld device designed to interact with a wide range of digital interfaces. Its primary purpose is to facilitate experimentation in cybersecurity, making it an ideal tool for fuzzing tasks. With its compact design and robust features, the Flipper Zero has gained popularity among security enthusiasts and professionals alike.
Equipped with a user-friendly interface, the Flipper Zero allows users to navigate its functionalities with ease. The device is capable of interacting with various protocols and frequencies, enabling it to engage with different systems and devices. This adaptability makes it particularly well-suited for fuzzing, as it can simulate a variety of attack vectors to test system resilience.
One of the standout features of the Flipper Zero is its open-source nature, which encourages community collaboration and innovation. Users can customize the device to suit their specific needs, allowing for tailored fuzzing experiences. This flexibility, combined with its powerful capabilities, positions the Flipper Zero as a valuable asset in the cybersecurity landscape.
How Does Flipper Zero Fuzzing Work?
Flipper Zero fuzzing leverages the device's unique capabilities to introduce unexpected inputs into a system, thereby testing its robustness. The process begins with selecting the target system or device that requires examination. The Flipper Zero then interfaces with the target, using its built-in tools and protocols to generate and transmit test inputs.
The fuzzing process can be tailored to specific requirements, allowing users to focus on particular areas of interest or concern. By manipulating the input parameters, users can simulate a wide range of scenarios, from minor anomalies to extreme cases. This comprehensive approach ensures that the system is thoroughly tested, revealing potential vulnerabilities that might otherwise remain hidden.
Read also:Rare Beauty Blush Elevate Your Makeup Routine With Effortless Elegance
Throughout the fuzzing process, the Flipper Zero monitors the system's response to the test inputs. Any anomalies or crashes are recorded and analyzed, providing valuable insights into the system's weaknesses. This information is crucial for developers and security professionals, as it enables them to address vulnerabilities and enhance the overall security of the system.
Why Use Flipper Zero for Fuzzing?
The Flipper Zero offers several advantages that make it an ideal choice for fuzzing tasks. Its versatility and adaptability allow it to interact with a wide array of systems and devices, making it suitable for diverse applications. This flexibility is particularly beneficial in fuzzing, as it enables users to test a broad range of scenarios and uncover hidden vulnerabilities.
Another key benefit of using the Flipper Zero for fuzzing is its user-friendly interface, which simplifies the testing process. Even those with limited technical expertise can navigate the device's functionalities with ease, making it accessible to a wider audience. This accessibility, combined with its powerful features, makes the Flipper Zero an attractive option for both beginners and experienced professionals.
The open-source nature of the Flipper Zero also contributes to its appeal. Users can customize the device to suit their specific needs, allowing for tailored fuzzing experiences. This level of customization is invaluable in cybersecurity, as it enables users to focus on particular areas of interest and develop targeted testing strategies.
Key Features of Flipper Zero
The Flipper Zero boasts a range of features that make it a standout tool in the field of fuzzing. These features include:
- Multi-Protocol Support: The Flipper Zero can interact with various protocols and frequencies, enabling it to engage with a wide range of systems and devices.
- User-Friendly Interface: The device's intuitive interface simplifies navigation and operation, making it accessible to users of all skill levels.
- Open-Source Customization: Users can modify the Flipper Zero to suit their specific needs, allowing for tailored fuzzing experiences.
- Portability: With its compact design, the Flipper Zero is easy to transport and use in a variety of settings.
- Community Collaboration: The open-source nature of the device encourages collaboration and innovation, leading to continuous improvements and updates.
Preparing for Fuzzing with Flipper Zero
Before embarking on a fuzzing project with the Flipper Zero, it is essential to prepare adequately to ensure a successful testing process. This preparation involves several key steps:
Identifying the Target System
Begin by identifying the system or device that requires fuzzing. This may include software applications, hardware systems, or network protocols. Having a clear understanding of the target system will guide the fuzzing process and help focus efforts on areas of interest.
Gathering Necessary Tools and Resources
Ensure that you have all the necessary tools and resources required for the fuzzing process. This may include additional software, cables, or other equipment needed to interface with the target system. Having everything ready will streamline the testing process and minimize disruptions.
Understanding the Flipper Zero's Capabilities
Familiarize yourself with the Flipper Zero's functionalities and capabilities. Understanding the device's strengths will help you leverage its features effectively during the fuzzing process. This knowledge will also enable you to customize the device to suit your specific needs.
Step-by-Step Guide to Flipper Zero Fuzzing
Embarking on a fuzzing project with the Flipper Zero involves a structured approach to ensure thorough testing and accurate results. Follow these steps to conduct a successful fuzzing project:
Step 1: Setting Up the Flipper Zero
Begin by setting up the Flipper Zero and ensuring it is ready for use. This involves charging the device, installing any necessary firmware updates, and configuring the settings to suit your testing requirements.
Step 2: Configuring the Fuzzing Parameters
Configure the fuzzing parameters to align with your testing goals. This includes selecting the type of inputs to be generated, determining the frequency and duration of the tests, and identifying any specific areas of interest within the target system.
Step 3: Conducting the Fuzzing Tests
Initiate the fuzzing tests by interfacing the Flipper Zero with the target system. Monitor the system's response to the test inputs, noting any anomalies or unexpected behaviors. Record these observations for further analysis.
Step 4: Analyzing the Results
Analyze the results of the fuzzing tests to identify potential vulnerabilities within the system. This analysis should include examining any errors, crashes, or unexpected behaviors triggered by the test inputs.
Step 5: Implementing Security Measures
Based on the findings from the fuzzing tests, implement necessary security measures to address the identified vulnerabilities. This may involve updating software, patching systems, or modifying protocols to enhance the system's resilience against potential threats.
Common Fuzzing Techniques
Fuzzing encompasses a variety of techniques, each designed to uncover specific types of vulnerabilities within a system. Some of the most common fuzzing techniques include:
Mutation-Based Fuzzing
Mutation-based fuzzing involves modifying existing inputs to create new test cases. This technique is effective in identifying vulnerabilities related to unexpected input formats or structures.
Generation-Based Fuzzing
Generation-based fuzzing involves creating new inputs from scratch based on predefined specifications. This technique is useful for testing systems with known input formats, as it allows for the creation of test cases that adhere to specific criteria.
Protocol Fuzzing
Protocol fuzzing focuses on testing communication protocols to identify vulnerabilities in data transmission and reception. This technique is particularly relevant for networked systems, as it helps ensure the security and integrity of data exchanges.
Flipper Zero Fuzzing in Cybersecurity
In the realm of cybersecurity, flipper zero fuzzing serves as a vital tool for identifying and addressing vulnerabilities within digital systems. Its ability to simulate a wide range of attack vectors makes it an invaluable asset for security professionals seeking to safeguard systems against potential threats.
The use of flipper zero fuzzing in cybersecurity extends beyond traditional software testing. It plays a crucial role in evaluating hardware systems, network protocols, and other digital interfaces. By uncovering vulnerabilities in these areas, flipper zero fuzzing helps organizations develop robust security measures that protect against unauthorized access and data breaches.
Moreover, flipper zero fuzzing supports proactive cybersecurity strategies by enabling organizations to identify and mitigate risks before they can be exploited by malicious actors. This proactive approach is essential in maintaining the security and integrity of digital systems in an ever-evolving threat landscape.
Challenges and Limitations of Flipper Zero Fuzzing
While flipper zero fuzzing offers significant benefits in identifying vulnerabilities, it is not without its challenges and limitations. Understanding these constraints is crucial for conducting effective fuzzing projects and managing expectations.
Complexity of Target Systems
One of the primary challenges in flipper zero fuzzing is the complexity of target systems. As digital systems become increasingly sophisticated, identifying and testing all potential vulnerabilities can be challenging. This complexity requires a comprehensive and strategic approach to fuzzing.
Resource Intensive
Fuzzing can be resource-intensive, requiring significant computational power and time to conduct thorough testing. This may limit the scope of fuzzing projects, particularly for organizations with limited resources.
False Positives and Negatives
Flipper zero fuzzing may produce false positives or negatives, leading to challenges in accurately identifying vulnerabilities. Careful analysis and validation of test results are essential to ensure the reliability of fuzzing findings.
Real-world Applications of Flipper Zero Fuzzing
Flipper zero fuzzing has a wide range of real-world applications, extending its utility beyond traditional software testing. Some notable applications include:
Embedded System Security
Flipper zero fuzzing is used to evaluate the security of embedded systems, identifying vulnerabilities that could be exploited to gain unauthorized access or compromise system functionality.
Network Protocol Testing
Flipper zero fuzzing is employed to test network protocols, ensuring the security and integrity of data exchanges between devices. This application is particularly relevant for organizations that rely on networked systems for operations.
IoT Device Security
As the Internet of Things (IoT) continues to expand, flipper zero fuzzing plays a crucial role in ensuring the security of IoT devices. By identifying vulnerabilities, it helps manufacturers and developers implement necessary safeguards to protect against potential threats.
The Future of Flipper Zero Fuzzing
The future of flipper zero fuzzing is promising, with continued advancements in technology and cybersecurity driving its evolution. Several trends and developments are expected to shape the future of fuzzing:
Increased Automation
As automation continues to advance, flipper zero fuzzing is likely to become more automated, allowing for more efficient and comprehensive testing processes. This automation will enable organizations to conduct fuzzing projects on a larger scale, enhancing their ability to identify vulnerabilities.
Integration with Artificial Intelligence
The integration of artificial intelligence (AI) and machine learning (ML) into flipper zero fuzzing is expected to enhance its capabilities, enabling more accurate and intelligent testing processes. AI and ML can assist in generating test cases, analyzing results, and identifying patterns that indicate potential vulnerabilities.
Expansion into New Domains
Flipper zero fuzzing is anticipated to expand into new domains, including emerging technologies such as blockchain and quantum computing. As these technologies evolve, fuzzing will play a crucial role in ensuring their security and integrity.
Best Practices for Effective Fuzzing
To maximize the effectiveness of flipper zero fuzzing, it is essential to follow best practices that ensure thorough testing and accurate results. Some key best practices include:
Defining Clear Objectives
Before embarking on a fuzzing project, define clear objectives that guide the testing process. This clarity will help focus efforts on areas of interest and ensure that the fuzzing project aligns with organizational goals.
Continuous Monitoring and Analysis
Throughout the fuzzing process, continuously monitor and analyze the results to identify potential vulnerabilities. This ongoing evaluation will help ensure that the fuzzing project yields reliable and actionable insights.
Maintaining Up-to-Date Knowledge
Stay informed about the latest advancements in fuzzing techniques and technologies to ensure that your fuzzing projects remain relevant and effective. This knowledge will enable you to leverage new tools and methodologies to enhance your testing processes.
FAQs about Flipper Zero Fuzzing
- What is the primary purpose of flipper zero fuzzing?
Flipper zero fuzzing is primarily used to identify vulnerabilities in digital systems by introducing unexpected inputs and observing the system's response.
- Can beginners use the Flipper Zero for fuzzing?
Yes, the Flipper Zero is designed with a user-friendly interface, making it accessible to beginners and experienced professionals alike.
- What types of systems can be tested with flipper zero fuzzing?
Flipper zero fuzzing can be used to test a wide range of systems, including software applications, embedded systems, network protocols, and IoT devices.
- What are the challenges associated with flipper zero fuzzing?
Some challenges of flipper zero fuzzing include the complexity of target systems, resource-intensive testing processes, and the potential for false positives or negatives.
- How does flipper zero fuzzing contribute to cybersecurity?
Flipper zero fuzzing helps identify and address vulnerabilities within digital systems, enabling organizations to implement necessary security measures and protect against potential threats.
- What is the future of flipper zero fuzzing?
The future of flipper zero fuzzing is expected to include increased automation, integration with AI and ML, and expansion into new domains such as blockchain and quantum computing.
Conclusion
Flipper zero fuzzing is a powerful technique for identifying vulnerabilities within digital systems, offering significant benefits in the field of cybersecurity. Its versatility and adaptability make it an ideal choice for a wide range of testing applications, from software and hardware systems to network protocols and IoT devices. By leveraging the capabilities of the Flipper Zero, users can gain valuable insights into their systems' weaknesses and implement necessary safeguards to enhance security and resilience.
As technology continues to evolve, flipper zero fuzzing is poised to play an increasingly important role in ensuring the security and integrity of digital systems. By staying informed about the latest advancements in fuzzing techniques and technologies, organizations can maximize the effectiveness of their fuzzing projects and safeguard their systems against potential threats. With its user-friendly interface and powerful features, the Flipper Zero remains a valuable asset in the ongoing effort to secure the digital landscape.
In conclusion, mastering the art of flipper zero fuzzing requires a comprehensive understanding of its methods, benefits, and applications. By following best practices and leveraging the capabilities of the Flipper Zero, users can conduct effective fuzzing projects that identify vulnerabilities and enhance the overall security of their systems. Whether you are a seasoned professional or a curious beginner, this guide provides the knowledge needed to harness the full potential of the Flipper Zero for fuzzing endeavors.